|
|
|
St Johns County Hurricane Preparedness |
|
City of St Augustine Hurricane Preparedness |
|
|
|
|
United States Local Channel Streaming News
Channels - During Comercial Breaks Some
Stations May Show A "Be Right Back" Message
Because of Commerical Ad Copywrite
Protections |
|
|
|
|
Emergency Actions Accidents -
Disasters |
|
|
Florida's Dangerous and Native
Species |
|
|
How to's and How Things Work |
|
|
Technology News & Information |
|
Atimatter - Quantum
Teleportation |
|
|
|
Technology News & Information for
Kids |
|
|
|
|
| The Chronological Evolution of the Boston Dynamics BIGDOG Robot - The Most Advanced Quadruped Robot on Earth compiled by Flicker 12/24/2014 |
| |
- Boston Dynamics LS3 Robot - World's MOST ADVANCED Military Robotics
- Published on Nov 26, 2013
|
|
|
"The goal of this machine is to go where the warfighter goes while carrying the load." — Kevin Blankespoor | chief engineer on the Legged Squad Support System project Marines test the capabilities of the Legged Squad Support System for the first time. |
|
| Marines with 1st Battalion, 5th Marine Regiment, put the system through its paces at Fort Devens, Mass., Nov. 5-7, 2013. The system, or LS3, is designed to reduce the load Marines carry in combat, can reach speeds of 6 mph and carry up to 400 pounds. The LS3 was created by Boston Dynamics with funding from the Defense Advanced Research Projects Agency (DARPA) and is currently being tested by the Marine Corps. Video by Sgt. Michael Walters | Defense Media Activity - Marines |
|
|
AlphaDog,
U.S.
Marines
Robot
Pack
Animal
-
Legged
Squad
Support
System
AiirSource
-
Marines
TV
Published
on
Jun
12,
2013
 |
The Marine Corps Warfighting Lab in partnership with the Defense Advanced Research Projects Agency and Boston Dynamics tested an autonomous robot on Joint Base Myer-Henderson Hall Sept. 10.
Alpha Dog- The Legged Squad Support System, or LS3, demonstration was a performance test of the pack mule prototype for the Commandant of the Marine Corps, Gen. James Amos and DARPA Director Arati Prabhakar.
Interviews include: Lt. Col Joe Hitt, DARPA program manager, and Brig. Gen. Mark R. Wise, Commanding General of the Marine Corps Warfighting Laboratory. Video by Cpl. Christofer Baines | Defense Media Activity - Marines |
| |
|
|
|
|
|
|
|
|
|
An Inkjet
Made My
Bladder! |
|
 |
|
Watch and
see how
tissues and
organs, such
as muscle
and
bladders,
are
custom-made
to replace
diseased or
injured
parts. |
|
May 16, 2008 |
|
|
|
|
|
|
|
|
What is a Bot? A Botnet? A Zombie Computer?
You may or may not have heard such terms as "Bots",
"Botnets", "Zombie Computer"
in news stories about data breaches and
other cybersecurity risks.
A "Bot", short for robot,
is a type of software application or script
that allows an attacker to take complete
control remotely of an affected computer.
The compromised machine may also be referred
to as a "Zombie", "Zombie Computer"
and a collection of these infected computers
is known as a "Botnet".
Millions of computers
worldwide are infected with Bots
and under the control of hackers as part of
a Botnet, which is a network
of computers running Bots
under the control of a
Botnet Operator.
Bots
are software applications that run
automated scripts over a network, while a
Botnet Operator
is a person controlling and maintaining the
Botnet.
The owners of these infected computers
typically do not experience any signs that
the machine is infected and continue to use
it, unaware they are being controlled by a
cybercriminal.
In fact, the infected machine
could be sending multiple spam emails,
including ones to all contacts in the
computer, making it appear that the email is
legitimate and from someone they know. They
can use your computer for mining Bitcoins or
other Cryptocurrencies; they can steal
banking passwords and can be used to infect
other computers on the Internet as well.
|
How does a Bot infection happen?
Bot
infections
follow the same path as the typical Internet
Virus or Worm.
A Computer Virus
is a malicious software program loaded
onto a user's computer without the user's
knowledge which performs malicious actions,
infects your programs and files, and alters
the way your computer operates or stops it
from working altogether.
A Computer Worm
is a type of malware that spreads copies of
itself from computer to computer. A computer
Worm can replicate itself without any human
interaction, and it does not need to attach
itself to a software program in order to
cause damage.
Malware
(Malicious Software) is any software
designed to cause harm. Malware can damage
files, steal sensitive data, and even take
your device hostage.
You may open an attachment in an
email, visit a malicious web site or
download malicious software often associated
with “free software” such as games,
screensavers, any of which may result in
malware being installed on your computer.
Once infected, the Bot
software sends a notice to the “controller”,
the Botnet Operator, who then
downloads additional malicious software to
the compromised host. The Botnet
controller then may have complete control of
your computer.
Examples of malicious software
commonly associated with Botnets and
the subsequent activity impact on your
computer are:
|
-
Programs that are used to distribute
spam. The next email you receive
regarding a hot stock tip or
prescription drugs could be coming from
your neighbor. These emails usually
employ a ”spoofed” or phony email
address.
-
Denial of service attack programs. The
botnet controller can summon tens of
thousands of zombies to overwhelm web
sites, computers or entire networks.
Even large companies such as Microsoft,
Yahoo and the New York Times have had
their web sites impacted by denial of
service attacks.
-
Use your computer for mining Bitcoins or
other Cryptocurrencies.
-
It is estimated that over 65% of spam
worldwide is sent by botnets.
-
The FBI recently reported a botnet
containing over one million zombie
computers!
How can I tell if my computer is part of a
botnet?
lIf
you are infected
with a worm or virus, chances are today that
you may also be part of a Botnet.
hSome
of the symptoms
of infection are:
-
Your computer and Internet connection
are slower than usual; programs that use
to run on your computer no longer are
able to run; your hard drive is spinning
(making a noise) and you are not using
your computer; Sluggish behavior by your
computer or any other strange behaviors
or anomalous activity on a computer.
-
You receive unexplained error messages
and your computer crashes frequently and
your computer takes longer to shut down
and startup
-
You discover messages in your outgoing
email folder that you didn’t send. A
tip-off might be if you receive
bounce-back notifications from people
you don’t know or haven’t emailed.
-
Your Web browser frequently closes for
no obvious reason and your access to
computer security websites is blocked.
-
CPU Usage at or near 100%
|
If you detect any of the above symptoms
affecting your computer that may be an
indication of an infection and should be
investigated further to determine if there
is an infection, and if so, the type and the
scale of the infection.
What can I do to protect my computer?
Bots propagate by taking advantage
of security vulnerabilities in software,
poor security controls, as well as by using
social engineering techniques to entice
users to open an email attachment that
infects your computer or to visit a web site
that downloads malware.
The following recommendations will
help prevent your computer from becoming
part of a botnet:
-
Never
open an email attachment unless you know
what it is--even if it's from someone
you know and trust.
-
Do not
visit untrusted web sites.
-
Do not
download free software from untrusted
sites.
-
Do not
use free file sharing programs. These
are commonly used to distribute music
files and often contain malware.
-
Use a firewall to filter Internet
traffic.
-
Use anti-virus
and anti-spyware software and keep it up
to date.
-
Keep your operating system and
application software, especially your
Internet browser, up-to-date.
|
|
What is a
computer Virus?
by
Flicker Thomas -
flicker@flickertronics.com
A
Computer Virus is a program or piece of
binary code
that is
loaded on to your computer without your
knowledge and can cause malicious
damage. All Computer Viruses are
man-made.
Some
Computer Viruses can also replicate
themselves
(Polmorphic Virus), and some types of
viruses are capable of transmitting
themselves across networks and bypassing
security systems.
Computer Viruses are often spread
through downloads
on the Internet or by attachments in
Email or instant messaging messages.
They can also be disguised as
attachments of funny images, greeting
cards, or audio or video files. That is
why it is essential that you open email
attachments unless you know who it's
from and you are expecting it.
|
What is
Ransomware?
by
Flicker Thomas -
flicker@flickertronics.com
Ransomware
is a type of Malware which blocks
access to the to the computer system that it
infects , and demands a ransom be paid to
the creators of the Malware via an
on-screen alert in order for the victim to
regain access to their computer or files,
typically in the $100 to $300 range.
Some forms of Ransomware will
put up an alert that the FBI has blocked
your computer and tell you to buy a MoneyPak
Card and put in the redemtion code to access
your computer - those are all bogus and
simply take your money.
Some forms of Ransomware
encrypt the files on the systems's hard
drive ( cryptoviral extortion).
The Cryptolocker Virus is
particularly nasty, and I will discuss that
in the article below.
|
Computer Workstation Ergonomics
Excerpts Compiled from OSHA
by
Flicker, CEO, Flickertronics
Millions
of people work with computers every day
and pay little attention to computer
workstation ergonomics, the study of how
people work in their environment and the
effects of such work on the human body.
While
there is no single correct
posture,
furniture arrangement or working
environment, with these few tips you will
find your workplace more comfortable.
Here are the tips:
1.
Keep top of
monitor at or just below eye level.
2.
Keep head and
neck balanced and in-line with torso.
3.
Keep
shoulders relaxed.
4.
Keep elbows
close to your body and supported.
5.
Keep lower
back supported.
6.
Keep wrists
and hands in-line with forearms.
7.
Have more
than adequate room for keyboard and mouse.
8.
Keep your feet flat on the floor.
9.
Have good
lighting and avoid glare from improperly
shaded windows. |
|
|
|
The Microsoft Imposter Scam
The Microsoft Impostor Scam
is Targeting the Saint Augustine,
Florida area especially hard in
recent months.
We have a number of people each
month who let impostors access their
computer remotely.
We have been receiving increased
calls from local consumers who have
been targeted by the Microsoft
Imposter Scam and similar others - a
number of them have allowed the
impostor to access their computers
remotely, and even paid, the
impostors!
The scam, which involves people
pretending to be employed by
Microsoft, Cisco, Linksys, HP or
other recognizable technology names
offering to fix computer Viruses, is
thought to have ripped off tens of
thousands of people in six
countries.
We will use Microsoft as an example,
but this applies to any such
suspicious caller since none of
those companies ever call people in
such a manner.
The Impostor will make an
unsolicited phone call, send a
letter, e-mail or text coming "out
of the blue" pretending to be a
Microsoft or other prominent company
employee. The targeted victim is
told that it has been detected that
their computer is infected with
Viruses and the caller offers to
help to fix the problem. |
The fake Microsoft employee will try to
“Hard Sell” their targeted victim regarding
all sorts of bad things that will happen to
their computer if they do not sort out the
problem immediately.
To
try to gain the targeted victims trust, the
caller may sometimes direct them to the Event Viewer
in Windows which shows
details about various hardware and Windows
software issues.
The Event Viewer
is
always full
of some type of error messages, even on a
healthy computer, but the caller will
convince them that these are the warning
signs of the impending disaster.
When the caller has their trust, they ask
the targeted victim to go to a website and
download a remote control program that will
help them fix the problem.
After downloading the remote control
program, the caller will take control of the
computer, the targeted victim will see their
mouse pointer move around while various
programs and folders are opened. The caller
will claim that they know exactly what the
problem is and how to fix it.
Then the caller will ask for credit card
details for a piece of software that will
supposedly remove the ‘Virus’.
The software that
they sell to fix the computer will do
nothing except tell you every now and then
that everything is fine, all viruses have
been removed. But in reality, it could be
downloading all sorts of Malware to your
computer. |
However, part of
the scam’s damage may already have been done
when the customer downloaded the remote
control software. This software could well
have the capability to sit in the background
for months or years, stealing personal
information from the computer like bank
login details and other personal details
that could be used for identity theft
purposes.
Quote from Microsoft:
"Microsoft takes
the privacy and security of our customers
and partners personal information very
seriously. We are advising customers to
treat all unsolicited phone calls with
skepticism and not to provide any personal
information to anyone over the phone or
online. Anyone who receives an unsolicited
call from someone claiming to be from
Microsoft should hang up. We can assure you
Microsoft does not make these kinds of
calls.”
These callers could also be using this
software to infect your computer
with real viruses and Malware.
If you receive one of these unsolicited
phone calls
hang up and do not download anything they
ask you to download.
And definitely don’t hand over your credit
card details,
just because someone mentions the well known
names Microsoft or Windows.
|
If
you have allowed them to take control of
your computer, or you have downloaded their
‘fix’ software, it is possible they have
infected your computer with a Virus or other
nasty Malware.
At
www.techsourcenews.com
we have a number of tools to verify that
your computer is safe and secure.
To scan and remove Viruses, Rootkits and Malware for FREE
from your computer, click on the Free Do
it yourself Virus Removal Tools link at
the top of the page.
Ransomware does not only target home
computers, thousands of businesses have been
infected as well, resulting in millions of
dollars in losses.
Paying the ransom does not guarantee your
encrypted files will be unencrypted, and
rarely does paying the ransom work..
However, if paying the ransom does work that
will start the decryption process. When you
pay the ransom you will be shown a screen
stating that your payment is being processed
and may take several hours to complete.
Once the payment has been verified, it will
begin decrypting your files, which can take
quite a while depending on how many files
were encrypted, and you most likely will not
recover many files!
|
|
US_CERT Security
Tip (ST06-003) - Staying Safe on
Social Network Sites |
What are social
networking sites?
Social networking sites, sometimes
referred to as "friend-of-a-friend"
sites, built upon the concept of
traditional social networks where
you are connected to new people
through people you already know.
The purpose of some networking sites
may be purely social, allowing users
to establish friendships or romantic
relationships, while others may
focus on establishing business
connections.
What security
implications do these sites
represent?
Some social networking sites
rely on connections and
communication, so they encourage you
to provide a cetain amount of
personal information. When decicing
how much information to reveal,
people may not exercise the same
amount of caution as they would in
person because
1. The Internet provides a sense of
anonymity
2. The lack of physical interaction
provides a false sense of security.
3. They tailor the information for
their friends to read, forgetting
that others may see it.
4. They want to offer insights to
impress potential friends or
associates
While the majority of people using
these sites do not pose a threat,
malicious people may be drawn to
them because of the accessibility
and amount of personal information
that's available. The more
information malicious people have
about you, the easier it is for them
to take advantage of you. Predators
may form relationships online and
then convince unsuspecting
individuals to meet in person
leading to potentially dangerous
situations.
|
The personal information can also be
used to conduct a social engineering
attack. Using information that you
provide about your location,
hobbies, interests, and friends, a
malicious person could impersonate a
trusted friend or convince you that
they have the authority to access
other personal of financial data.
Additionally, because of the
popularity of these sites, attackers
may use them to distribute malicious
code. Sites that offer applications
developed by third parties are
particularly susceptible. Attackers
may be able to create customized
applications that appear innocent
while infecting your compute or
sharing your information without
your
knowledge. (High Security Risk for
business networks - Flicker)
Limit the amount of personal
information you post - Do not post
information that would make you
vulnerable, such as your address or
information about your schedule or
routine. If your connections post
information about you, make sure the
combined information is not more
than you would be comfortable with
strangers knowing. Also be
considerate when posting information
, including photos, about your
connections.
Remember that the Internet is a
public resource - Only post
information you are comfortable with
anyone seeing. This includes
information and photos in your
profile and blogs and other forums.
Also, once you post information
online, you can't retract it. Even
if you remove the information from a
site, saved or cached versions may
still existon other people's
machines.
Be wary of strangers - The Internet
makes it easy for people to
misrepresent their identities and
motives. Consider limiting the
amount of people who can contact you
on these sites. If you interact with
people you do not know, be cautious
about the amount of information you
reveal or agreeing to meet them in
person
Be Skeptical - Don't believe
everything you read online. People
may post false or misleading
information about various topics,
including their own identities. This
is not necessarily with malicious
intent; it could be unintentional,
an exaggeration, or a joke. Take
appropriate precautions, though, and
try to verify the authenticity of
any information before taking
action.
Evaluate your settings - Take
advantage of a site's privacy
settings. The default settings for
some sites may allow anyone to see
your profile, but you can customize
your settings to restrict access to
only certain people. There is still
a risk that private information
could be exposed despite these
restrictions, so don't post anything
ou would not want the public to see.
Be wary of third-party applications
- Third-party applications may
provide entertainment or
functionality, but use caution when
deciding which applications to
enable. Avoid applications that seem
suspicious, and modify your settings
to limit the amount of information
the applications can access.
|
|
Use strong passwords - Protect your
account with passwords that cannot
easily be guessed. If your password
is compromised, someone else may be
able to access your account and
pretend to be you.
Check privacy policies - Some sites
may share information such as email
addresses or user preferences with
other companies. This may lead to an
increase in spam. Also, try to
locate the policy for handling
referrals to make sure that you do
not unintentionally sign your
friends up for spam. Some sites will
continue to email messages to anyone
you refer until they join.
Keep software, particularly your
web browser, up-to-date -
Install software updates so that
attackers cannot take advantage of
known problems or vulnerabilities.
Many operating systems offer
automatic updates. If this option is
available, you should enable it.
Use and maintain Antivirus software
- Antivirus software helps protect
your computer against known viruses,
and some offer added protection from
"Viruses in the Wild", or unknown
viruses, using Heuristics. Because
attackers are continually writing
new viruses, it is important to keep
your definitions up to date.
|
|
|
|
|
Flicker’s Story
“Mom,
I hear voices in the in the oven”
by Flicker Thomas
Being
in business for over 21 years I have had hundreds and hundreds
of people ask me how I became interested in
electronics.
This is the wondrous tale that started me upon my path.
“Mom,
I hear voices in the in the oven”.
I was almost 6 years old, and we had just moved to Jacksonville,
Florida.
As a child I
was always into everything, reading, poking and prying into
things. One day I opened the door to our electric oven and heard
voices. I ran into the other room and yelled for my mom to come
into the kitchen and told her I heard voices coming from the
oven.
We walked into
the kitchen and opened the oven door and there was complete
silence. My mom just gave me a puzzled look and walked back into
the living room and sat back down.
Over the next
few weeks I kept hearing music and voices in the oven, and each
time I summoned my mom, dad or my sister the music would stop.
Mom, Dad and my sister were finally convinced that I had some
mental illness or affliction that was getting worse.
Then one day
my mom was standing in the kitchen near me when I decided to
open the oven door and see what would happen. I heard people
talking and called for my mom to come over. She just stood there
and gave me a look of sorrow and pity for her poor sick child.
In desperation I went to her and dragged her by the arm and
screamed for her to listen.
She stuck her
head in the open oven door and heard music for a few seconds.
The look on her face was utter shock since she was experiencing
the same delusions her poor, sick child had been. Over the next
few days or so everyone was sticking their heads in the oven to
hear the people talking and the music playing briefly for a few
seconds. Then one day we heard them announce WAPE and discovered
we were hearing the local AM radio station less than one half
mile away.
I was
mesmerized by the thought that you could hear a radio station in
your electric oven. I had to find out how this could possibly
happen so I went to the library and started my quest for
knowledge (which has never ended)
I learned that
when two pieces of metal are touching and are oxidized
(corroded) they can actually function as a rectifier, which Is
a diode detector, and generate sound like a Cat’s Whisker
Crystal Radio Detector, which was used in early radio Sets (The
Cat’s Whisker was a small piece of wire – no cats were ever
harmed!). The close proximity of the local AM radio station is
what made this feat possible! This phenomenon only occurs with
AM (Amplitude Modulated) radio signals, and not in FM radio
(Frequency Modulated) signals.
The term
“Cats’ Whisker” refers to a thin wire that lightly touches a
crystal of semiconducting mineral (a rectifier or
Diode Detector,
which is usually made from galena) to make a crude point-contact
rectifier.
|
|
|
|
Diagram
of a
crystal radio from 1922 using a cat's-whisker
detector |
Modern
galena cat's-whisker detector, showing parts. The galena
crystal (upper left) is held in the metal capsule with a
screw cap, leaving its face exposed. |
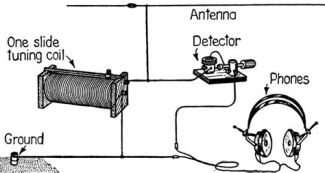

From then on I read everything
I could about electronics and electricity that was available.
This is a prime example of how children can be affected by
things they are exposed to early in life.
Thank you
for reading,
Flicker
Thomas
flicker@flickertronics.com
|
|
The
Cloth Stretcher Incident
by Flicker Thomas
- As a teenager, at age 19
my best friend and I got a job at the furniture company
where my father had worked for years. Our job consisted of
loading couches and other furniture into semi-trailers. It
was late summer and it was so hot outside, and inside, they
had water sprinklers on the tin roof and big, industrial
size fans strategically located inside to make the working
conditions tolerable.
-
- One day after I had been
working there for a week or so my boss came up to me and
said “I need for you to
- bring me the cloth
stretcher” and walked back towards his office.
-
- I walked away from the
loading dock and started my search. I went up to the first
person’s station near the
- loading dock and asked
where I could find the cloth stretcher. He gave me a nice
smile said to ask the next person in line.
-
- Every person I went to
just smiled as I inquired as to where the cloth stretcher
was, and each suggested that perhaps the next person down
the line would know.
-
- For 30 or so minutes I
continued my search for the elusive cloth stretcher, finding
no one who knew where it was. With my mission an apparent
failure, I reflected upon how nice each person had been and
how their faces lit up when I asked them where the object of
my search might be.
-
- Having asked everyone in
the warehouse as well as the furniture builders I went back
to the first person I had asked. By now I had been on my
quest for at least 45 minutes with no success.
-
- I asked him for the
second time “Do you know where the cloth stretcher is?”
-
- By now everyone in the
business had their eye on me and what I was doing, and I
felt I was under intense scrutiny, appearing to be the focus
of everyone’s attention.
-
- He looked at me with a
funny, quirky smile and said “Look, I have to tell you that
there is no such thing as a cloth stretcher”.
- I looked at him and gave
a huge, great smile and said “YOU know there is no such
thing as a cloth stretcher and I know there is no such thing
as a cloth stretcher, but what would you do? Look for
something your boss asked you to find or load trucks in this
heat.”
-
- My smile widened as I saw
the utterly stunned look on his face, then he started
laughing and laughing.
-
- I went to the loading
dock, picked up a sofa and balanced it on my head and
started loading the truck again.
-
- This business was around
for over 20 years and I was the first person to turn a
newcomer prank around.
-
-
-
-
-
Thank you for reading,
-
Flicker Thomas
-
flicker@flickertronics.com
|
|
- This Ad-Free Website and
Ad-Free Newspapers are Sponsored by Flickertronics
-
- Broadband Cable and Fiber Optic Internet
-
Flickertronics is a Comcast Business and AT&T Solution Provider
-
Ever used an Insurance Broker, or a Real Estate Broker?
-
- Why not a Telecom Broker?
-
-
Let an unbiased broker work on your behalf to find the optimal services for your company.
-
-
We may be able to improve your existing Internet and Telecom services while lowering your monthly bills.
-
-
- Flickertronics Represents Over 75 Internet, Data, Telecom, VoIP, and Cloud Service providers, offering businesses lower costs by cutting out the "Middleman",
- your local Reseller or Phone Man.
-
-
Representing the major carriers directly, acting as their agent, we can provide the following services at no cost to you:
-
-
Free unbiased analysis of your current Internet and Telephone services.
-
Free unbiased quotes from all the current Telecommunications and Internet providers in your area.
-
Free 24x7x365 Concierge Support and On-Site Service for carrier Internet or Telecom issues from pre-quote, and before, during, and after
Installation.
|
|
-
-
We work with senior channel partners at the corporate level
- Comcast
- Airespring
- AT&T
- Level3
Lumen
|
- HughesNet Satellite
- T-Mobile Business
- ViaSaT
-
Time Warner Business Class
- Verizon Business
|
- Starlink
- Spectrum Business
- DirecTV For Business
- RackSpace
|
-
-
Flickertronics works through high level Dedicated Partner Channel Managers, and Senior Partner Relationship Managers.
-
-
Working through Corporate Officers assigned to Partner Relations, Flickertronics bypasses their sales departments, which operates from a "Canned" script
-
and has company sales incentives to get you to purchase additional products and services, and have no authority.
-
-
A Comcast Business Solution Provider brings immense value to businesses by serving as their single point-of-contact for their connectivity and technology needs.
-
-
We are also an AT&T Solution Provider as well and hold similar postitions with all 75+ providers.
-
-
We also provide VoIP phone service only from Enterprise Class Carriers with recognized names - avoid VoIP resellers with their "Own" brand.
-
-
For more information please contact Flicker Thomas:
- (904)825-6708
- flicker@flickertronics.com
-
|
|
Installed Revolver Maps 12/10/2024 |
All Rights Reserved
copywrite 1997-2024 Flickertronics
www.flickertronics.com
|